Welcome to part two of my post. Previously I spoke about building a security system using a Raspberry Pi Zero and MotioneyeOS. (Read Here) I built and installed the system in February and it was working great. I even caught some Ass-Hat driving over my lawn and trash (Read Here). I ran into one issue with this system. Once Summer was here and the outside temperatures hit 90° (32°c) The processor temperature of the Pi Zero was topping 161° (72°C) and lack of cooling was causing my Pi Zeros to crash
According to the Raspberry Pi foundation the boards are specked to approach 80°C but mine were failing in the mid 70’s. So now to work on a solution.
How to cool your outdoor Motioneye camera
My first attempt was an obvious one – Paint the camera white.
The waterproof boxes I was using to house the camera had a clear cover. To reduce the amount of sunlight, I simply painted the box white
Painting the box was helpful and kept the system cooler , but it still wasn’t enough. The next step was to vent the box simply by drilling a few small holes at the bottom. I know this compromises my “waterproof” concept, but I am hedging my bets if any rain water was to enter the box, it would remain at the bottom and not touch the electronics.
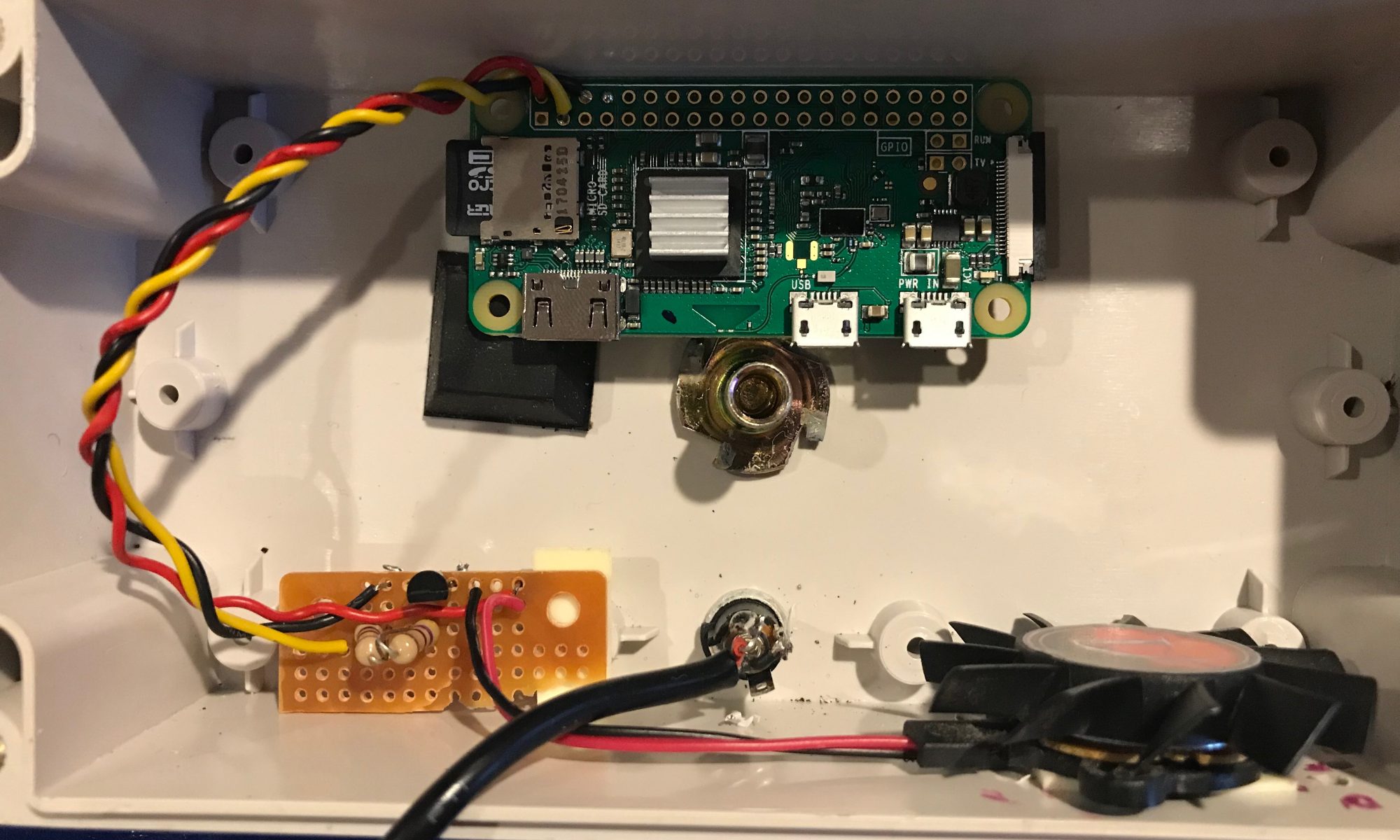
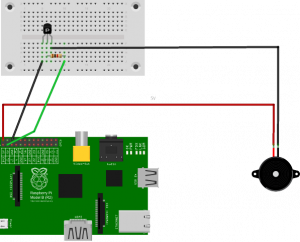
Still not good enough! I want to add a fan, but I only want the fan to run when the CPU hits a specific temperature. There is no need to run the fan on cool nights or during the winter. So I decided to use the GPIO pins on the PI Zero to control the fan.
Controlling the cooling fan via GPIO pins
Parts List
- 5 Volt cooling fan
- 1 NPN Transistor
- 1 1KΩ Resistor (or equivalent)
- Small breadboard
- Soldering iron / solder
How to assemble
Its probably not a good idea to connect a fan directly to one of the GPIO pins, so I used a simple transistor and resistor to help limit the current being drawn via the pin
 Continue reading “Cooling your Motioneye Pi Zero Security Camera”
Continue reading “Cooling your Motioneye Pi Zero Security Camera”