Recently a colleague at my day job fell for a scam email that appeared to be from PayPal. She clicked and entered all the info they requested and at the very end realized she had been taken for a ride. This post will cover some of the things you can look for to help identify a scam “phishing email” .Many of you are able to identify a phishing email in seconds, but if I can help one person identify a scam its worth the effort to write this post.
1. English as a second language
A good portion of attacks originate in non-English speaking countries. The hackers generate a phishing email that may be grammatically correct in their language, however when translated using google translate some of the message is lost in translation.
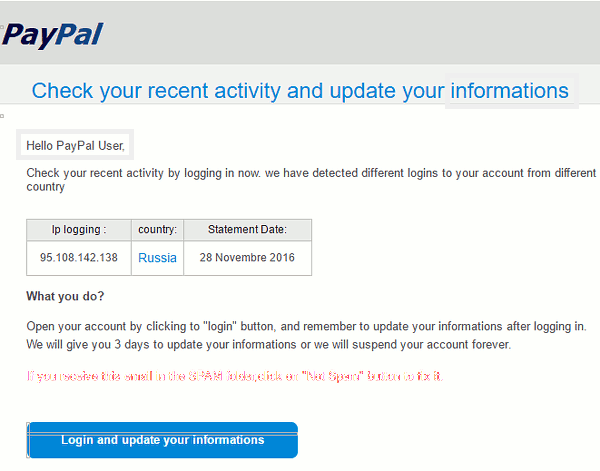
In the above example we are asked to update our “informations” this was supposedly written by someone at PayPal, not a third grader. PayPal would never allow such a message to be sent to their customers. If it sounds wrong, it most likely is wrong!
2. If I’m such a valued customer, call me by my name.
All of the companies that you do business with know you by name, and they are going to call you by name when they correspond with you. Once again in the above example “Hello PayPal User” this is a total give away! Also be on the look out for “Dear Valued Customer”, “<insert bank name here> preferred customer”. On occasion the phishers try to guess your name based on your email address, as in the Amazon example below. The give away is they put my name in all caps.
3. Who sent that email?
A good portion of the country has made a purchase from Amazon.com and this makes Amazon a good subject / target for phishing emails. I personally receive a few dozen fake Amazon messages a day. This week Amazon is giving me a $200 credit as an Easter gift – Yeah RIGHT!
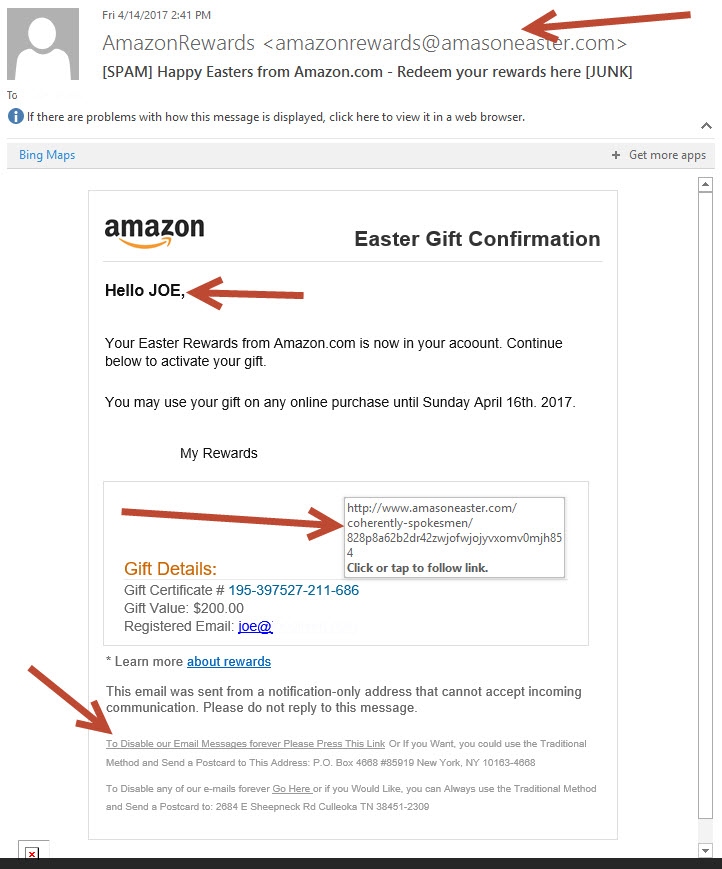
This email has so many things wrong with it, I would be amazed if anyone actually clicked on it.
As the heading to this section says “Who sent that email?” Just look at the domain that sent the message @amaSoneaster.com. WTF? Who is Ama-Son-Easter LOL.
TECH ALERT – a brief explanation as to why the phisher used amasoneaster and not just amazon.com as the sending domain.
Phishers have to resort to “alternate” domains due to increased use of email security measures like SPF (Sender Policy Framework). SPF is a system that publishes the servers identity that are allowed to send mail for a particular domain. For example, when my ISP or corporate mail server receives an email from Amazon.com we immediately look fora published SPF record. If the published record matches the server that sent the email, the message is thought to be authentic. If the sending server does not match the SPF list, the message is classified as SPAM.
4. The hover link test.
Most email clients like Outlook will display the contents of a link before you click on it. Simply hover your mouse pointer over the link and carefully examine the destination. In the Amazon example above you can see the link even looks phishy. Again the domain is wrong and what is a coherently-spokesmen. Just looks very wrong to me.
http://www.amasoneaster.com/coherently-spokesmen/828p8A62B2drdfdfdfdf42zwjOFwjOjyvXOmv0Mjh854
When using a browser based mail service such as gmail or yahoo the link will appear at the bottom of your browser while hovering.
5. The format just looks wrong
The unsubscribe section of the above Amazon message is also a dead giveaway. First off why is it in the message twice? Plus they are both different with different snail mail addresses asking us to “use the Traditional Method” Are they giving us instructions on getting pregnant or unsubscribe instructions. The grammar is not horrible here, but the general syntax is not something we would normally say, plus capitalization is wrong as well.
6. Using mail headers to identify a phishing message (advanced)
This might be a little technical for some, however a good method to identify where a message originated is by examining the message header. The header is a hidden part of the message that provides a trail of how the message got from the sender to your inbox. Each mail client has its own way of displaying the headers, google for your mail client for instructions.
Received: from 130.185.254.132 ([130.185.254.132])
Fri, 14 Apr 2017 14:00:58 -0400
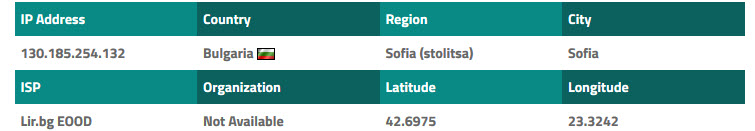
After examining the message header I was able to obtain the IP address of the sending server. A quick geolocation lookup of the IP address reports that the sending server is in Bulgaria. It is possible that Amazon has servers in Bulgaria, however its highly unlikely.
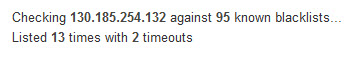
The last test I ran was to see if the IP address was listed on an email black list. Yes, it was positive for sending spam.
Summary
When you receive an unsolicited message from a company you normally do business with, be weary of the message so you don’t fall victim to a scam. Remember these tips and you will be ready to spot all the phish in the sea!
- Check for proper grammar and syntax, if it sounds like broken English its probably a scam.
- Who sent the message, if its not from a domain you would expect its most likely bogus.
- Look for subtle changes in email addresses learn@yahoo.com is not the same as Iearn@yahoo.com (first one has an “L” second one has a capital “i”)
- Hover over the links, do they go to the website you would expect?
- Does the overall formatting look wrong?
- Trust your spam filter, if the message was routed to your junk mail folder there may be a good reason.
- Be your own hacker and track that message back to the source with the IP address in the mail header and geolocation tools on the web.
Thanks for reading.
Questions – ideas@webcommand.net
-Joe
Don’t forget to visit my Etsy store



One Reply to “6 Simple tips to AVOID email phishing scams!”