I have been a big fan of SonicWall products for the last 18 years. Even after being taken over by Dell, I still use Sonicwall in my office and at home. You may say its overkill to have one in my home, but I tend to model my home lab environment to my office environment. I like to think of my home network as a sandbox for testing things in the office.
This year we are making a big push for better security around the office and one topic that came up was the office WiFi. Currently the office Wifi shares the same LAN connection as the rest of the network. Even worse there is only one SSID for both the staff and guests. Even worse than that the SSID password has not been changed for 10+ years!
A project was commissioned to segment the WiFi network from the LAN, however it is important to allow the staff that works in the office access to the LAN via WiFi when needed.
Equipment RequireD
Sonicwall – I have a NSA2600, but any modern NSA device will do. If you’re not sure which Sonicwall to purchase, this is a great starter.
 Sonicwall TZ300 Total Secure $679.99 at Amazon
Sonicwall TZ300 Total Secure $679.99 at Amazon
WiFi Access points. I happen to really like the Ubiquiti access points. Centrally managed, mesh network, great performance and very reliable.
Ubiquiti Access point – long range $98.00 at Amazon
If you go with the Ubiquity access points they come with POE (power over Ethernet) injectors. Note – If you buy a multi pack they DO NOT come with POE injectors, only the individual box sets do.
Don’t want to be bothered with POE injectors, Ubiquity makes a few really good POE switches. Depending on how many access points you need there is a POE switch for you. If you’re working on a small installation this switch supports 4 POE connections.
Ubiquiti UniFi Switch 8port (4 POE) $109.00 at Amazon
Hooking it all up:
In a typical Sonicwall setup the X0 port would be your LAN, and the X1 port would be your WAN. In this scenario we would be using the X2 port for our WiFi network.
The first thing I did was add a ZONE to my Sonicwall
Network -> Zones -> Add
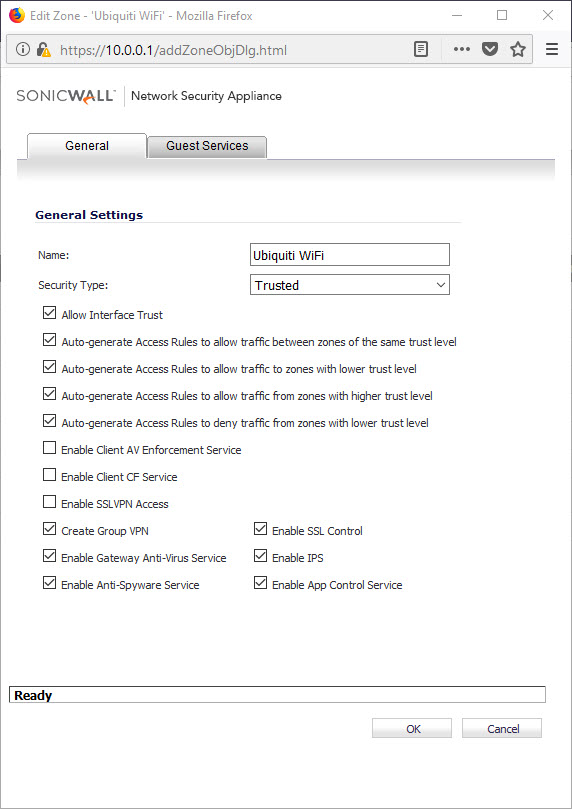
Then I applied that Zone to one of my interfaces X2, X3, ETC.. you pick.
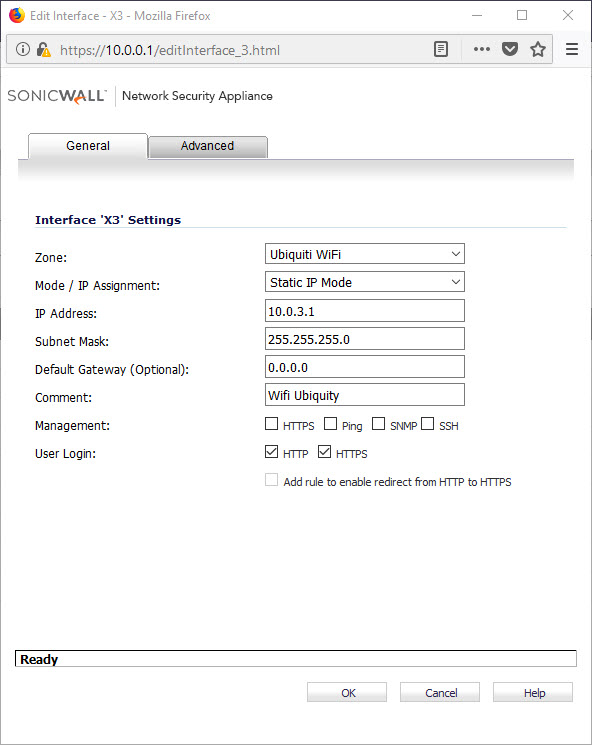
You may need to set up a DHCP server for the new WiFi segment.
Add a DHCP server and assign the range to the interface of your WiFi installation (X2 or X3 etc..)
Once this has been completed you should be able to access the internet via Wifi and it will be completely separate from your LAN
Allow access for staff from Wifi to Lan
In some instances the staff may want to cross from the Wifi subnet to the LAN subnet.
In this case we need a method to authenticate users who would like LAN access. Within the SonicWall there is the ability to setup a user table containing our local users. When setting up users be sure to place them in the Trusted Users group <- Very Important
Next go to Firewall -> Access Rules and add a rule that allows trusted users to access the LAN from the WiFi (see below)
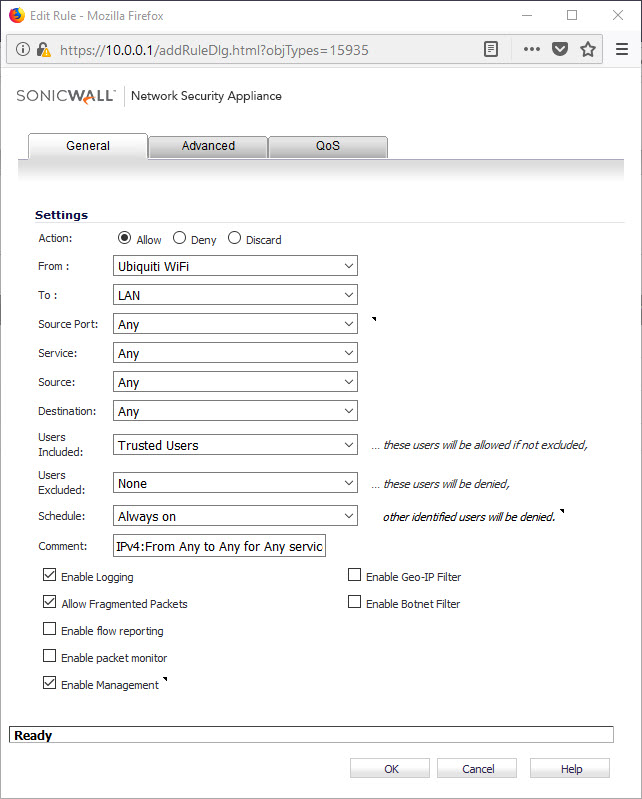 The above rule will allow users to cross from Wifi to your LAN by authenticating to the SonicWall, and the user has to be a member of the TRUSTED USERS group.
The above rule will allow users to cross from Wifi to your LAN by authenticating to the SonicWall, and the user has to be a member of the TRUSTED USERS group.
How do my end users achieve this?
To make this as painless as possible, add an “A” record to your DNS on the Wifi subnet
in A 10.0.3.1 sonicwall.mydomain.com
Inform your users to open a web browser and access sonicwall.mydomain.com they will be greeted with a user name and password on a secure webpage.
 Login and you’re good to go. The session time limits can be tweaked in the SonicWall settings.
Login and you’re good to go. The session time limits can be tweaked in the SonicWall settings.
Other things to consider
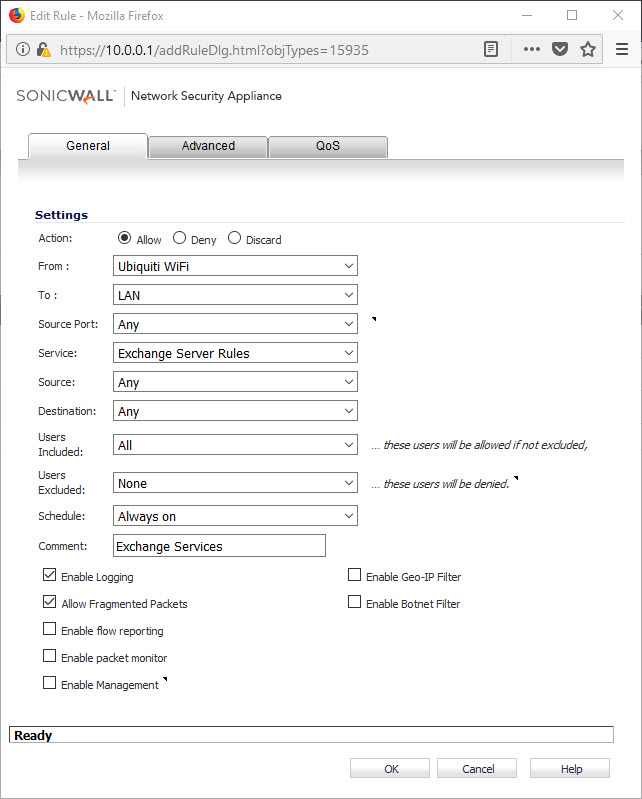
You can add other rules to allow access to internal resources without forcing users to authenticate. Maybe there is an intranet server you would like to access, or what about Exchange Active Sync (if your hosting an exchange server on the LAN)
I have a few extra rules set up to allow the same Wifi -> LAN access as i would allow WAN -> LAN. this way the experience of moving from Wifi in the office to say Wifi at home is seamless for my users
This is an example of a rule setup to allow Exchange Active sync and Webmail / OWA
On final thought about accessing the Sonicwall via the web interface. The NSA units come with a self signed certificate that your browser is going to choke on as not trusted. You can simply add a security exception to every users browser, or just go to namecheap.com or your registrar of choice and purchase an SSL certificate for $9.00 to eliminate this issue.
That’s all I have for now!
I hope you enjoyed my blog,
Thank you – Joe
Don’t forget to hit up my Etsy store
https://www.etsy.com/shop/geekgear